Tech giant Microsoft uncovered an attack targeting crypto startups using a pdf file that uses the names OKX, Binance, and Huobi.
The pdf file is titled “OKX, Binance & Huobi VIP fee comparison.xls.” and includes a malicious code that allows the attackers to access the victim’s software remotely, and run an excel macro in invisible mode on the background.
The attack
According to the document, Microsoft detected that the attacker had infiltrated chat groups on Telegram and pretended to be the representative of the exchange platforms in question.
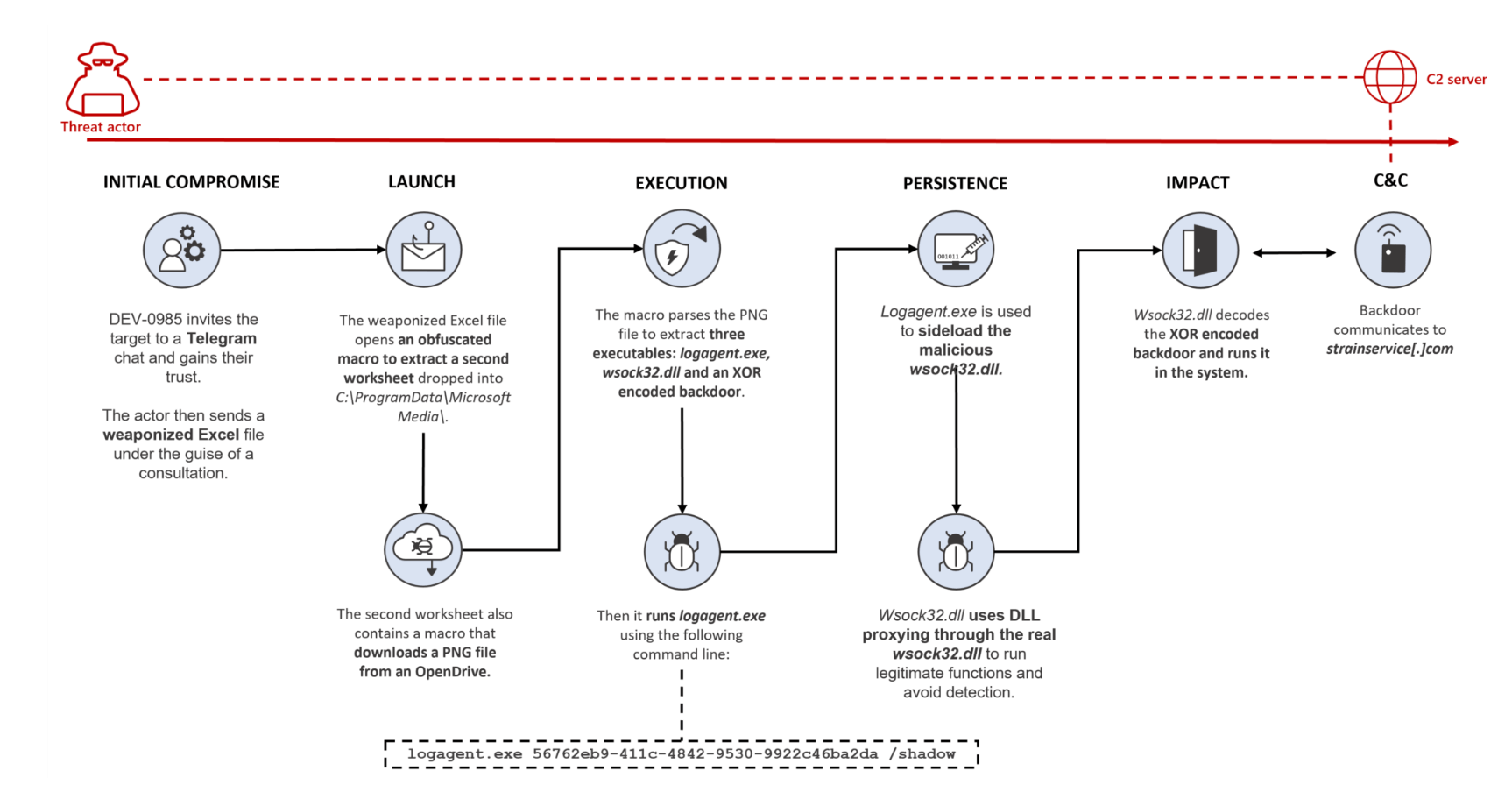
It was realized that the attacker had in-depth knowledge in the matter as well, which he utilized to gain the trust of various crypto companies. Afterwards, the attacker convinced its victims to download the document in question.
Microsoft also warned that there might be other actors that use a similar method to infiltrate into systems.



